The configuration of Wireguard on DEBIX is divided into two parts, the first part: you need to recompile the linux-debix kernel (address: https://github.com/debix-tech/linux) on the PC to enable the wireguard driver, and then add the wireguard driver to DEBIX; the second part: configure wireguard on DEBIX.
Note: The attached kernel file is already compiled. If you don't want to recompile the kernel, please copy the appendix WireGuard file into the /lib/modules/5.10.72 folder of DEBIX; then you can skip the PC operation part.
PC operation section:
Software tool: MobaXtrem
Download address: MobaXterm free Xserver and tabbed SSH client for Windows.
(https://mobaxterm.mobatek.net/download.html)
1. Download DEBIX kernel on the PC to enable WireGuard application.
(1) Install git dependencies:
sudo apt install git bc bison flex libssl-dev make
(2) Download the source code:
git clone --depth=1 GitHub - debix-tech/linux: Kernel source of DEBIX kernel
(3) Export the environment variables:
export CROSS_COMPILE=~/tools/gcc-arm-9.2-2019.12-x86_64-aarch64-none-linux-gnu/bin/aarch64-none-linux-gnu-
export ARCH=arm64
(4) Go to the source directory and generate the default configuration file:
cd debix-kernel
make imx_v8_defconfig
(5) Enter menuconfig interface and configure the Wireguard items
make menuconfig
- The kernel version is 5.10.72, enter the Device Drivers item:
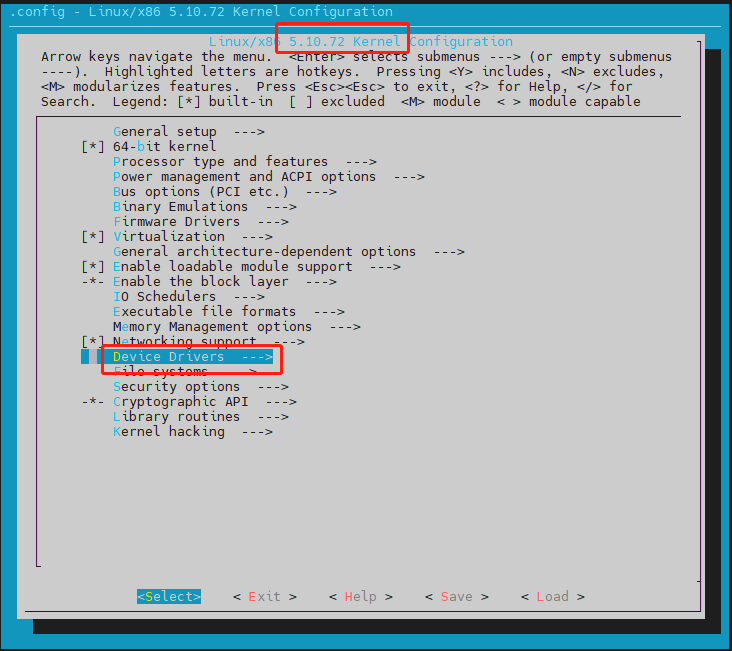
- Select Network device support item

- Enable modular WireGuard secure network tunnel

Set to "M", then save and exit.
2. Compile the kernel on the PC and generate the wireguard.ko file
(1) Compile the kernel source code:
make -j4
(2) Compile kernel modules:
make modules
(3) Install the kernel module to out directory:
make INSTALL_MOD_STRIP=1 modules_install INSTALL_MOD_PATH=out
By comparing the pre-compilation and post-compilation kernel driver modules, the following driver module files are added after compilation:
a: 5.10.72/kernel/net/ipv6 ---- ip6_udp_tunnel.ko
b: 5.10.72/kernel/net/ipv4 ---- udp_tunnel.ko
c: 5.10.72/kernel/lib/crypto ---- libcurve25519-generic.ko
d: 5.10.72/kernel/lib/crypto ---- libcurve25519.ko
e: 5.10.72/kernel/lib/crypto ---- libchacha20poly1305.ko
f: 5.10.72/kernel/lib/crypto ---- libblake2s-generic.ko
g: 5.10.72/kernel/lib/crypto ---- libblake2s.ko
h: 5.10.72/kernel/drivers/net/wireguard ---- wireguard.ko
i: 5.10.72/kernel/arch/arm64/crypto ---- poly1305-neno.ko
j: 5.10.72 ---- modules.builtin.alias.bin
(4) File replacement:
a. Copy the extra driver files compiled in step (3) to the corresponding directory in DEBIX.
b. Replace the driver module mounting dependency file: /5.10.72/modules.dep, /5.10.72/modules.dep.bin
Replace the dependency files in the compiled kernel file with the two dependency files in the /lib/modules/5.10.72/ folder of DEBIX.
DEBIX operation section:
3. Install and configure Wireguard on DEBIX
(1) Update the application:
apt-get update
(2) Install wireguard:
apt install wireguard
(3) Check whether the installation is successful:
modprobe wireguard && lsmod | grep wireguard
If the installation is successful, it will display:

(4) Configure the wireguard server:
- Create the wireguard directory
mkdir /etc/wireguard
- Enter the directory:
cd /etcwireguard
- lGenerate a pair of public and private keys via the command
wg genkey | tee privatekey | wg pubkey > publickey && cat privatekey && cat publickey

(5) Wireguard PC-to-DEBIX configuration:
- First download WireGuard exe on the PC, download address:
https://www.wireguard.com/install/; According to the system you are using to choose to download, here choose for Windows.
- Second, open Wireguard, create a new tunnel, edit the configuration file.

- Then, fill in the information generated on DEBIX to the configuration file on the PC.
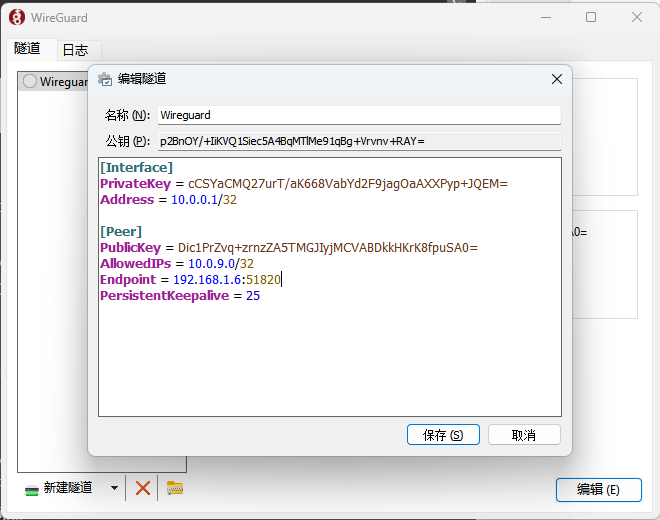
The content of the configuration file is described as follows:
[interface]
PrivateKey: client’s privateKey
Address: the virtual IP address of the client
[Peer]
PublicKey: the publicKey generated on DEBIX
AllowedIPs: the virtual IP addresses of DEBIX
Endpoint: IP address and listening port number of DEBIX
persistenKeeppalive: upload heartbeat packet interval(s)
Click Save when the configuration is complete.
(6) Get the publickey on the PC, configure the client file on DEBIX:
- Create a new wg0.conf in the /etc/wireguard folder
vim wg0.conf
- Fill in the configuration file content
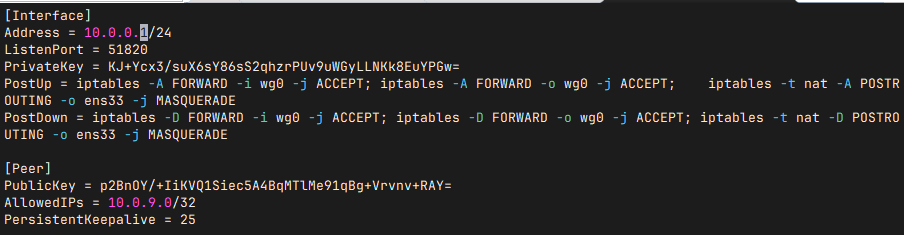
- Save and exit.
[Interface]
PrivateKey = #DEBIX server's private key
Address = #virtual address of the server
ListenPort = #The port number to listen on
#The following firewall settings need to correspond to the actual network card name, which may be something like ens33.
PostUp = iptables -A FORWARD -i wg0 -j ACCEPT; iptables -A FORWARD -o wg0 -j ACCEPT; iptables -t nat -A POSTROUTING -o ens33 -j MASQUERADE
PostDown = iptables -D FORWARD -i wg0 -j ACCEPT; iptables -D FORWARD -o wg0 -j ACCEPT; iptables -t nat -D POSTROUTING -o ens33 -j MASQUERADE
[Peer]
PublicKey = #client's public key
AllowedIPs = #IP address of the client's virtual network card
PersistentKeepalive = 25 #upload heartbeat packet interval(s)
wg

(8) Start wireguard:
wg-quick up wg0
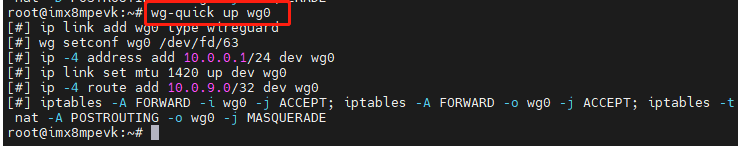
Result:
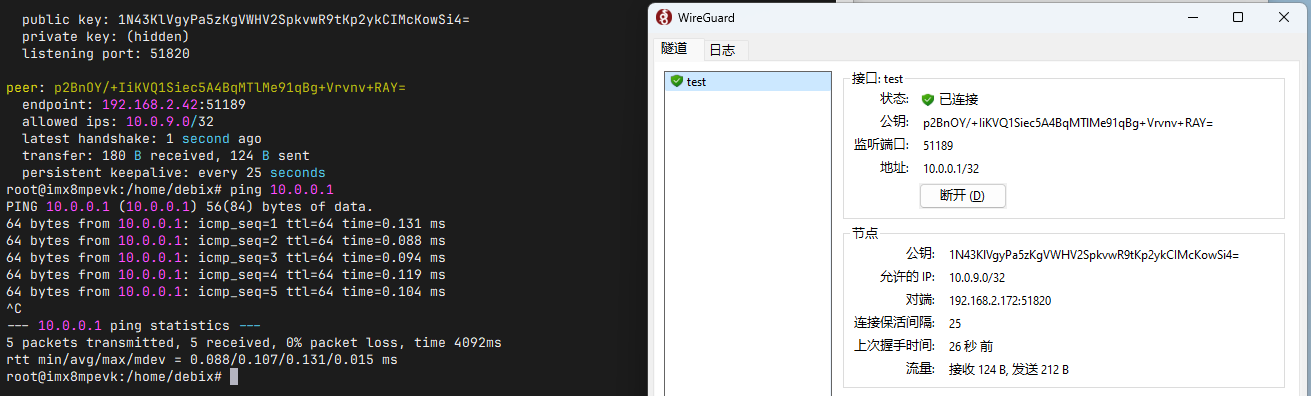
(9) Exit wireguard:
wg-quick down wg0
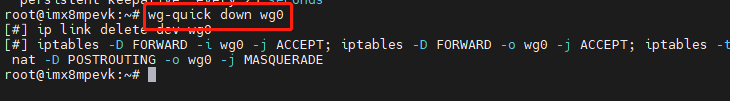
The above is the completion of installing and running wireguard on DEBIX.












